Xiao steganography
Author: s | 2025-04-24

Download xiao. Xiao Steganography . Xiao Steganography; Steganography l nghệ thuật ngụy trang hoặc ẩn.
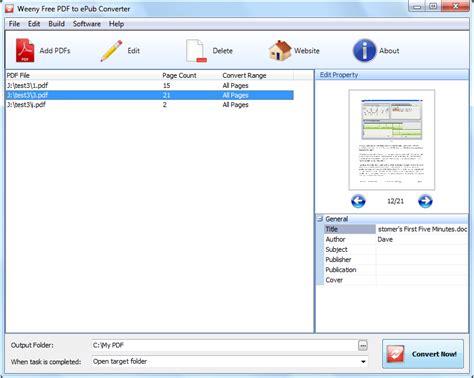
Xiao steganography Xiao Steganography is free software that
Should I remove Xiao Stenography?What percent of users and experts removed it?8% remove it92% keep itWhat do people think about it?Be the first to rate (click star to rate)VersionsVersionDistribution2.6.1100.00% What is Xiao Stenography? (from Nakasoft)Steganography is the art of covered or hidden writing. The purpose of steganography is covert communication to hide a message from a third party. This differs from cryptography, the art of secret writing, which is intended to make a message unreadable by a third party but does not hide the existence of the secret commu... Read moreOverviewXiao Stenography 2.6.1 is a program developed by Nakasoft. The main program executable is xiao_steg.exe. In comparison to the total number of users, most PCs are running the OS Windows 10 as well as Windows 7 (SP1). While about 81% of users of Xiao Stenography come from the United States, it is also popular in Argentina and Australia.Program detailsURL: www.nakasoft.netInstallation folder: C:\Program Files\xiao stenographyUninstaller: C:\Program Files\Xiao Stenography\uninst.exeFiles installed by Xiao Stenography 2.6.1Program executable:xiao_steg.exeName:Xiao SteganographyPath:C:\Program Files\xiao stenography\xiao_steg.exeMD5:e72aefbb78d42ad3792b782d45bd8011Additional files:uninst.exeHow do I remove Xiao Stenography?You can uninstall Xiao Stenography from your computer by using the Add/Remove Program feature in the Window's Control Panel.On the Start menu (for Windows 8, right-click the screen's bottom-left corner), click Control Panel, and then, under Programs, do one of the following:Windows Vista/7/8/10: Click Uninstall a Program.Windows XP: Click Add or Remove Programs.When you find the program Xiao Stenography 2.6.1, click it, and then do one of the following:Windows Vista/7/8/10: Click Uninstall.Windows XP: Click the Remove or Change/Remove tab (to the right of the program).Follow the prompts. A progress bar shows you how long it will take to remove Xiao Stenography.OS VERSIONSWin 10 47%Win XP 12% USER ACTIONSUninstall it 8%Keep it 92% US RANK#41,320WindowsWhich Windows OS versions does it run on?Windows 1047.06%Windows 741.18%Windows XP11.76%Which OS releases does it run on?Windows 7 Home Premium17.65%Windows 7 Ultimate17.65%Microsoft Windows XP11.76%Windows 8.111.76%Windows 8.1 Enterprise11.76%Windows 10 Education5.88%Geography81.48% of installs come from the United StatesWhich countries install it? United States81.48% Argentina3.70% Australia3.70% DK3.70% Spain3.70% United Kingdom3.70%PC manufacturersWhat PC manufacturers (OEMs) have it installed?Toshiba28.57%Intel21.43%Hewlett-Packard21.43%Acer21.43%ASUS7.14%Common modelsVMware, Inc. VMware Virtu...18.18%TOSHIBA Satellite S55t-C9.09%TOSHIBA Satellite Pro C50...9.09%TOSHIBA Satellite C55D-B9.09%TOSHIBA Satellite C55-A9.09%Hewlett-Packard p6-2427c9.09% Download xiao. Xiao Steganography . Xiao Steganography; Steganography l nghệ thuật ngụy trang hoặc ẩn. Xiao Steganography, free and safe download. Xiao Steganography latest version: A free Security program for Windows. Xiao Steganography is a great, fr One, is called the Least Significant Bit. Hackers use this bit to embed malicious code because the overall pixel value will be reduced by only one, and the human eye can’t detect the difference in the image. So, no one is even aware that anything is amiss, and that the image is carrying something dangerous within.Palette-Based TechniqueLike the Least Significant Bit technique, the Palette-Based Technique also relies on images. Hackers embed their message in palette-based images such as GIF files, making it difficult for cybersecurity threat hunters or ethical hackers to detect the attack.Various tools or software that support steganography are now readily accessible. Though most hide information, some provide additional security by encrypting it beforehand. You can find the following free steganography resources online:Steghide: Steghide is a free tool that uses steganography to conceal information in other files, such as media or text.Stegosuite: It is a Java-based, free steganography tool. Stegosuite makes it simple to obfuscate data in pictures for covert purposes.OpenPuff: It is a high-quality steganographic tool that allows you to conceal data in other media types like images, videos, and Flash animations.Xiao Steganography: To conceal information in BMP images or WAV files, use the free Xiao Steganography tool.SSuite Picsel: The free portable program SSuite Picsel is yet another option for hiding text within an image file; however, it uses a somewhat different method than other programs.These are only a few of the steganography tools available. However, these instruments will help you achieve your goals.Advantages of SteganographySteganography is a method that makes it easy to conceal a message within another to keep it secret. The result is that the hidden message remains hidden. A steganography approach can benefit images, videos, and audio files. Further advantages include:Unlike other methods, steganography has the added benefit of hiding communications so well that they receive no attention. However, in countries where encryption is illegal, sending an encrypted message that you can easily decipher will raise suspicion and may be risky.Steganography is a form of encryption that protects the information within a message and the connections between sender and receiver.The three essential elements of steganography—security, capacity, and robustness—make it worthwhile to covert information transfer via text files and develop covert communication channels.You can store an encrypted copy of a file containing sensitive information on the server without fear of unauthorized parties gaining access to the data.Government and law enforcement agencies can communicate secretlyComments
Should I remove Xiao Stenography?What percent of users and experts removed it?8% remove it92% keep itWhat do people think about it?Be the first to rate (click star to rate)VersionsVersionDistribution2.6.1100.00% What is Xiao Stenography? (from Nakasoft)Steganography is the art of covered or hidden writing. The purpose of steganography is covert communication to hide a message from a third party. This differs from cryptography, the art of secret writing, which is intended to make a message unreadable by a third party but does not hide the existence of the secret commu... Read moreOverviewXiao Stenography 2.6.1 is a program developed by Nakasoft. The main program executable is xiao_steg.exe. In comparison to the total number of users, most PCs are running the OS Windows 10 as well as Windows 7 (SP1). While about 81% of users of Xiao Stenography come from the United States, it is also popular in Argentina and Australia.Program detailsURL: www.nakasoft.netInstallation folder: C:\Program Files\xiao stenographyUninstaller: C:\Program Files\Xiao Stenography\uninst.exeFiles installed by Xiao Stenography 2.6.1Program executable:xiao_steg.exeName:Xiao SteganographyPath:C:\Program Files\xiao stenography\xiao_steg.exeMD5:e72aefbb78d42ad3792b782d45bd8011Additional files:uninst.exeHow do I remove Xiao Stenography?You can uninstall Xiao Stenography from your computer by using the Add/Remove Program feature in the Window's Control Panel.On the Start menu (for Windows 8, right-click the screen's bottom-left corner), click Control Panel, and then, under Programs, do one of the following:Windows Vista/7/8/10: Click Uninstall a Program.Windows XP: Click Add or Remove Programs.When you find the program Xiao Stenography 2.6.1, click it, and then do one of the following:Windows Vista/7/8/10: Click Uninstall.Windows XP: Click the Remove or Change/Remove tab (to the right of the program).Follow the prompts. A progress bar shows you how long it will take to remove Xiao Stenography.OS VERSIONSWin 10 47%Win XP 12% USER ACTIONSUninstall it 8%Keep it 92% US RANK#41,320WindowsWhich Windows OS versions does it run on?Windows 1047.06%Windows 741.18%Windows XP11.76%Which OS releases does it run on?Windows 7 Home Premium17.65%Windows 7 Ultimate17.65%Microsoft Windows XP11.76%Windows 8.111.76%Windows 8.1 Enterprise11.76%Windows 10 Education5.88%Geography81.48% of installs come from the United StatesWhich countries install it? United States81.48% Argentina3.70% Australia3.70% DK3.70% Spain3.70% United Kingdom3.70%PC manufacturersWhat PC manufacturers (OEMs) have it installed?Toshiba28.57%Intel21.43%Hewlett-Packard21.43%Acer21.43%ASUS7.14%Common modelsVMware, Inc. VMware Virtu...18.18%TOSHIBA Satellite S55t-C9.09%TOSHIBA Satellite Pro C50...9.09%TOSHIBA Satellite C55D-B9.09%TOSHIBA Satellite C55-A9.09%Hewlett-Packard p6-2427c9.09%
2025-04-17One, is called the Least Significant Bit. Hackers use this bit to embed malicious code because the overall pixel value will be reduced by only one, and the human eye can’t detect the difference in the image. So, no one is even aware that anything is amiss, and that the image is carrying something dangerous within.Palette-Based TechniqueLike the Least Significant Bit technique, the Palette-Based Technique also relies on images. Hackers embed their message in palette-based images such as GIF files, making it difficult for cybersecurity threat hunters or ethical hackers to detect the attack.Various tools or software that support steganography are now readily accessible. Though most hide information, some provide additional security by encrypting it beforehand. You can find the following free steganography resources online:Steghide: Steghide is a free tool that uses steganography to conceal information in other files, such as media or text.Stegosuite: It is a Java-based, free steganography tool. Stegosuite makes it simple to obfuscate data in pictures for covert purposes.OpenPuff: It is a high-quality steganographic tool that allows you to conceal data in other media types like images, videos, and Flash animations.Xiao Steganography: To conceal information in BMP images or WAV files, use the free Xiao Steganography tool.SSuite Picsel: The free portable program SSuite Picsel is yet another option for hiding text within an image file; however, it uses a somewhat different method than other programs.These are only a few of the steganography tools available. However, these instruments will help you achieve your goals.Advantages of SteganographySteganography is a method that makes it easy to conceal a message within another to keep it secret. The result is that the hidden message remains hidden. A steganography approach can benefit images, videos, and audio files. Further advantages include:Unlike other methods, steganography has the added benefit of hiding communications so well that they receive no attention. However, in countries where encryption is illegal, sending an encrypted message that you can easily decipher will raise suspicion and may be risky.Steganography is a form of encryption that protects the information within a message and the connections between sender and receiver.The three essential elements of steganography—security, capacity, and robustness—make it worthwhile to covert information transfer via text files and develop covert communication channels.You can store an encrypted copy of a file containing sensitive information on the server without fear of unauthorized parties gaining access to the data.Government and law enforcement agencies can communicate secretly
2025-03-28Are many kinds of dedicated software applications available to facilitate steganography. Here is a partial list of the more well-known steganography applications:Image Steganography: This application is a JavaScript tool used to hide images in other image filesOpenStego: This program is an open-source steganography toolXiao Steganography: Xiao hides secret files in WAV or BMP filesCrypture: This application is a command-line tool used to conduct steganographyNoClue: This application is an open-source tool that hides text information in both video and image carrier filesSteganography Master: This app is an Android-based open-source tool that can hide text in an image and gives you a decoding tool to pull hidden text messages from image files. It supports multiple image formats (BMP, JPG, ICO, PNG)Steghide: Steghide is an application that hides data in different audio and image files, including JPEG, BMP, AU, and WAVAre You Interested in a Cyber Security Career?Whether you’re interested in steganography or not, cyber security is a field with a lot to offer for someone who wants an exciting challenge mixed in with a great career that offers security and excellent benefits.Simplilearn’s Post Graduate Program in Cyber Security is designed to teach you the skills you need to become an expert in the fast-growing field of cyber security. The course offers you a comprehensive approach to protecting your organization’s infrastructure and securing its data, including topics like cloud-based security, risk analysis and mitigation, and compliance. In addition, you will gain a range of skills from foundational to advanced via industry-leading cyber security certification courses.This course is well-suited for professionals who want to upskill since it helps you stay abreast of all the latest cybersecurity trends. However, if upskilling is your priority, you should consider widening your cybersecurity-related skill range by taking Simplilearn’s CISSP Certification Training Course and developing your expertise in defining IT architectures and in designing, building, and maintaining secure business environments, using globally approved information security standards.According to Indeed, Network Security Engineers in the United States earn about USD 114,060 a year. Meanwhile, in India, a Security Analyst who has cyber security skills can earn an average of ₹491,643 per year, according to Payscale.As for the mystery message above, read it again, but take note of the first letter of each sentence. That’s an example of steganography. Can you see the top-secret message now? That paragraph is a form of an acrostic, a composition with a hidden word or phrase,
2025-04-14În această nouă eră cibernetică, securitatea informației este cel mai important lucru și toată lumea dorește să își securizeze datele. Haideți să vorbim despre software-ul de steganografie care este disponibil și complet gratuit pentru a fi descărcat.Acest software de steganografie ne permite să ascundem date (textuale sau fișiere de diferite formate) în fișiere de imagine. Nu numai atât, dar, de asemenea, aceste instrumente sunt capabile să ascundă fișiere precum DOCX, XLSX, ZIP, RAR etc.1.QuickStego2.Xiao Steganography3.OpenStego4.Camouflage5.Steghide1.QuickStegoQuickStego este un software de steganografie gratuit. Acesta le permite utilizatorilor să ascundă cu ușurință texte sub formă de imagini. Cele mai bune formate de suport de intrare sunt BMP, JPG, JPEG și GIF. De asemenea, este suficient de bun pentru a salva imaginile de ieșire în mai multe formate. Interfața software-ului este prietenoasă cu utilizatorul.Download Link2.Xiao SteganographyXiao Steganography este unul dintre cele mai simple, dar eficiente software-uri de steganografie existente. Acesta este bun pentru imagini BMP sau în fișiere WAV cu suport pentru criptare. Cu acesta, este ușor să direcționați fișierul BMP sau WAV către interfața sa, urmat de clic pe fișierul secret. Nu numai atât, dar suportă și algoritmi de criptare precum RC4, Triple DES, DES, DES, Triple DES 112, RC2 și algoritmi de hashing SHA, MD4, MD2, MD5.Download Link3.OpenStegoOpenStego este un software ușor și uimitor. Tipurile de fișiere pe care le acceptă sunt BMP, GIF, JPEG, JPG, PNG și WBMP. Lucrul interesant este că acest software vă ajută să setați parolele, astfel încât sistemul dvs. să rămână protejat. Cu el, puteți efectua sarcini
2025-04-13Have you ever heard of the idea of hiding something in plain sight? Today’s security-conscious environment is the ideal place for trying out new techniques for hiding sensitive information. After all, we need to stay one step ahead of hackers and would-be data thieves!That’s why we are about to explore the concept of steganography, including what is steganography, what techniques it entails, and how it’s used in today’s cybersecurity efforts. So, let’s begin with a definition.What Is Steganography?A steganography technique involves hiding sensitive information within an ordinary, non-secret file or message, so that it will not be detected. The sensitive information will then be extracted from the ordinary file or message at its destination, thus avoiding detection. Steganography is an additional step that can be used in conjunction with encryption in order to conceal or protect data.Steganography is a means of concealing secret information within (or even on top of) an otherwise mundane, non-secret document or other media to avoid detection. It comes from the Greek words steganos, which means “covered” or “hidden,” and graph, which means “to write.” Hence, “hidden writing.”You can use steganography to hide text, video, images, or even audio data. It’s a helpful bit of knowledge, limited only by the type of medium and the author’s imagination.Although the technique is centuries old, it’s still useful enough to make us justifiably pose the question, “What is steganography in cyber security?” But before we explore its uses in today’s cyber security field, let’s get more acquainted with the overall concept by looking at some steganography examples, then wrap things up with a fun little exercise.Also Read: Why is Cybersecurity Important in 2022?Different Types of Steganography1. Text Steganography − There is steganography in text files, which entails secretly storing information. In this method, the hidden data is encoded into the letter of each word. 2. Image Steganography − The second type of steganography is image steganography, which entails concealing data by using an image of a different object as a cover. Pixel intensities are the key to data concealment in image steganography.Since the computer description of an image contains multiple bits, images are frequently used as a cover source in digital steganography.The various terms used to describe image steganography include:Cover-Image - Unique picture that can conceal data.Message - Real data that you can mask within pictures. The message may be in the form of standard text or an image.Stego-Image
2025-04-23AbstractThe internet has grown to be widely used by billions of individuals in our digital age. The internet is required for a variety of platforms, online apps, and standalone applications. Numerous methods, including cryptography, encryption/decryption, and data concealment algorithms, are developed for this goal. However, the employment of these methods was not very secure, making it simple for hackers to get the secret message. A new method called “steganography” was developed to offer the highest level of protection for sensitive data. Steganography's primary goal is to conceal the presence of concealed messages. Additionally, it seeks out concealed messages using factors like the kind of embedding method, the message's length, its content, or the carrier's secret key. At this point in the chapter, a single bit of data has been embedded into edge-based pixel positions with arbitrary bit positions. The authors have compared their method to three standard edge detection algorithms for a more comprehensive assessment. Different statistical measures also have been made for the uniqueness of the technique.TopIntroductionInformation security is regarded as one of the utmost crucial components of technology based on the exchange of information and messages due to the expansion of the Internet and computer technology in recent decades. Information security refers to the processes put in place by corporations to keep sensitive data secure. This entails installing safeguards to prevent unauthorized individuals. Information security encompasses a wide range of subjects, including but not limited to networking and security architecture, monitoring, and accounting. Information security safeguards vital records from being illegally accessed, modified, recorded, interrupted, or destroyed. Cryptography and steganography are one of the most crucial methods for protecting sensitive data (Safarpour et al.,2016). The intention of cryptography is to ensure that only the intended recipients of a message or transmission can decipher and utilize the data contained inside it (Kaur et al., 2010). This ensures that sensitive data remains secure from prying eyes. Steganography is the study of concealing information in unremarkable items such that an opponent cannot detect its presence (Dadgostar et al., 2016). To evade discovery, data may be steganographed by being buried inside an otherwise benign file or message. Confidential material may be recovered from a conventionally sent file or message after it has delivered at its recipient. In addition to encryption, steganography may be used to covertly hide or secure sensitive information. This technique involves concealing data or a hidden message inside another digital media file, such as a picture, song, or video (Pal et al., 2013). Its origins lie in the Greek words for “to write” (graph) and “covered” (steganos). As a result, we refer to it as “secret writing.”There are typically five distinct approaches in the steganography process namely audio steganography, text steganography, video steganography, image steganography and network/protocol steganography. Data concealment in text steganography is accomplished by encoding it into the alphabetic sequence of words. Steganography with images involves hiding information inside a picture of something else. Steganography in audio is the practice of concealing information using sound. The term
2025-04-07