Is web threat shield safe
Author: l | 2025-04-24
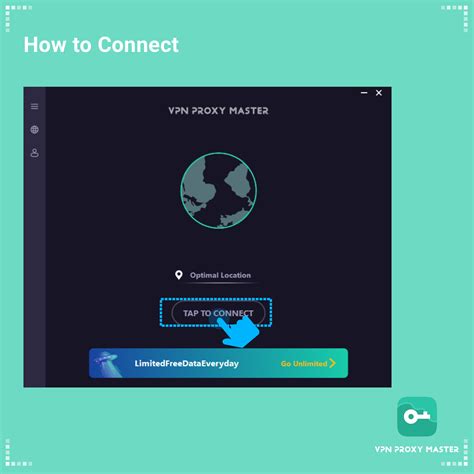
Keeps you safe when browsing the web by identifying and blocking dangerous websites. Home/ Productivity/ Web Threat Shield. Web Threat Shield Web Threat Shield
Web Threat Shield - Safe Web Browsing Chrome Extension
Scans data that is transferred when you browse the internet to prevent malware from being downloaded and run on your PC. Avast Geek settings allow you to specify which action Web Shield performs when it detects a threat (virus, potentially unwanted program, potentially unwanted tool, or suspicious object). For each individual threat type, select an action from the drop-down menu:Abort connection (selected by default): Terminates your connection with the applicable website as soon as a potential threat is detected.Ask: Gives you the option to terminate the connection with the applicable website or remain connected when a potential threat is detected. Remaining connected may be risky. The following options allow you to further configure Web Shield behavior:Scan traffic from well-known browser processes only: With this option enabled, Web Shield only monitors HTTP traffic for the most common browsers.Show a notification window when an action is taken (enabled by default): You receive a notification from Avast each time Web Shield detects a threat. Script Shield protectionScript Shield prevents browsers and other applications from running potentially malicious scripts. This includes remote threats from the web and outside sources, local threats downloaded to your hard drive or in the browser cache, and scripts that come from encrypted connections.Tick or untick the relevant box to specify which browsers and applications are protected by Script Shield. Commonly used browsers, Adobe Acrobat Reader, and all other applications on your PC are protected by default.You can additionally configure report file settings individually for Web Shield.QuarantineQuarantine is an isolated space where you can safely store potentially dangerous files or send them to the Avast Threat Labs for analysis. Avast Geek settings allow you to specify the maximum size of files that Avast sends to Quarantine. The default value is 16384 KB.FirewallFirewall monitors all network traffic between your PC and the outside world to protect you from unauthorized communication and intrusions. You can configure the following aspects of Firewall behavior:Show notifications about newly created "block" rules (enabled by default): Sends an alert message each time a new rule related to prohibiting communication is created by the auto-decide feature.Internet Connection Sharing mode: Allows a trusted user to connect to the internet through your PC, or to troubleshoot problems with devices, such as a printer that is connected to the internet via your PC. Ticking this option opens certain ports which are usually closed, decreasing the level of security. Always untick this
Web Threat Shield - learn.learningpartnership.org
Company Expands Ericom Global Cloud Platform Data Center Footprint to Support Growing Demand for Ericom’s Zero Trust Remote Browser Isolation SolutionNew York, NY (December 22, 2020) – Ericom Software, a leader in Zero Trust cloud cybersecurity solutions and a member of the Oracle Partner Network (OPN), announced today an expansion of its Ericom Global Cloud platform data center presence in the Middle East to support growing demand for Ericom Shield Remote Browser Isolation (RBI). These investments expand local access to Ericom’s globally distributed, multi-tenant cloud platform for businesses in the region, including existing Ericom customers supported by the company’s regional distribution and reseller partners. This announcement follows the company’s November press release noting it is experiencing record global demand for its Zero Trust security solutions as enterprises adopt Zero Trust and Secure Access Service Edge (SASE) security strategies.The rate of cyberattacks using malware designed to exploit web browser vulnerabilities has been dramatically accelerating. These types of attacks use zero-day malware embedded in the content of websites to deliver ransomware, exfiltrate data, disrupt operations, and more. The move to remote work, tied to COVID-19 office closures, unfortunately created additional vulnerabilities that make the risk of these attacks even greater. Ericom Shield RBI is uniquely capable of protecting endpoints and networks from just these sorts of attacks, preventing attacks targeting organizations via phishing emails, social media, and other stealthy vectors.Traditional web and email security approaches attempt to block threats by scanning traffic coming into networks, hoping to detect malware in order to protect devices. Ericom Shield RBI uses a fundamentally different approach that prevents 100% of web-based ransomware, zero-day threats, and phishing attacks from reaching endpoints. The solution executes web content in a remote, isolated cloud -based container, and only safe rendering information is sent to a device’s browser, providing a fully interactive, seamless user browsing experience. Whether users browse to a malicious site on their own or by clicking a URL embedded in a phishing email, they are completely safe since no web content is ever executed directly on their device.“Ransomware and other browser-based exploits delivered via the web and email are the key threat vectors that organizations need to secure,” said Ravi Pather, Ericom Vice President, Europe, and Middle East. “Ericom’s Zero Trust RBI solution integrates with solutions like secure web gateways and firewalls to ‘air gap’ endpoints from zero-day attacks being delivered by malicious websites that users visit whileWeb Threat Shield - Chrome Web Store
Avast One is the free, all-in-one service that combines antivirus, extra privacy (VPN), and security tools to help you stay private and safe anywhere you go online and on every device.• Make your connection to any network secure & private with a VPN• Stay safe from viruses & malware with an advanced antivirus• Find out if a password is compromised in a new data breach so you can quickly re-secure your online accountsDevice protection• Advanced antivirus: Automatically scan for viruses and other kinds of malware, including spyware, Trojans, and more. Web, file, and app scanning provide complete mobile security.• Virus cleaner: Safely remove viruses and malware from your phone. Uses real-time intelligence from the largest threat-detection network of 435 million Avast users.• Web Shield: Scan and block malware-infected links, as well as Trojans, adware, and spyware (for privacy and safe web browsing). Automatically fixes mistyped URLs so you avoid dangerous sites. • Wi-Fi Scanner: Check a network’s encryption and password strength so you can avoid joining a network where your safety or privacy would be at risk.Online privacy• Military-grade security: Make your connection to any network secure & private with a Virtual Private Network (VPN). • True online privacy: Hide your online activities so you can do what you want online without anyone finding out thanks to a VPN. • Access streaming while abroad: Stream your favorite movies and shows with access to your streaming subscriptions while traveling by using a VPN to change your device’s location to any of 35 countries.• Data Breach Monitoring: Scan new data breaches for leaked passwords linked with the email address you use to sign in to your online accounts. Find out if the email and password combination to any of your online accounts is compromised so you can quickly re-secure your accounts and prevent intruders from getting access.• Junk Cleaner: Make more space for your photos, videos, and music by cleaning out junk files with our most efficient cleaner yet. This app uses the Accessibility permission to protect visually impaired and other users against phishing attacks and malicious websites.. Keeps you safe when browsing the web by identifying and blocking dangerous websites. Home/ Productivity/ Web Threat Shield. Web Threat Shield Web Threat Shield Keeps you safe when browsing the web by identifying and blocking dangerous websites. Home/ Productivity/ Web Threat Shield. Web Threat Shield Webroot Inc. Web Threat ShieldWeb Threat Shield - Chrome Web Mağazası
Remove the file from your computer.Nothing: No action is taken during the scan; the threat is listed in your scan results and you can decide what to do later. The following options allow you to further configure File Shield behavior:You can additionally configure report file settings individually for File Shield.Mail ShieldMail Shield scans for threats in your incoming and outgoing email messages. Avast Geek settings allow you to specify which action Avast Antivirus performs when Mail Shield detects a threat (virus, potentially unwanted program, potentially unwanted tool, or suspicious object). For each threat type, select an action from the drop-down menu:Auto (selected by default): Run a sequence of actions (repair file; if not possible, then move to Quarantine; if not possible, then delete)Ask: Avast asks what you want to do with a detected threat before any action is taken.Nothing: No action is taken during the scan; the threat is listed in your scan results and you can decide what to do later.Move to Quarantine: Send the threat to Quarantine, where it cannot harm your system.Repair: Remove only malicious code attached to an otherwise safe file; this is not possible for files that are entirely malware.Delete: Permanently remove the file from your computer. The following options allow you to further configure Mail Shield behavior:Show a notification window when an action is taken (enabled by default): You receive a notification from Avast each time Mail Shield detects a threat.Scan archived messages when opening: Scans archived messages every time they are opened.Scan SSL connections (enabled by default): Enables scanning of emails sent or received using SSL/TLS encrypted connection. If disabled, only emails sent or received via unsecured connections are scanned. Export a Mail Shield certificateClick Perform to export a Mail Shield certificate from Avast Antivirus. This is useful for troubleshooting error messages about invalid server certificates from third party email clients, such as Mozilla Thunderbird.Port settingsIf Avast fails to intercept a malicious email or you notice that you are not receiving certain emails, you may need to correct the defined port numbers. Avast Geek allows you to edit the port numbers according to your email service provider or mail server configuration.If you do not know the port numbers that your mail service uses, contact your email provider or network administrator, or refer to the settings section of your email client.You can additionally configure report file settings individually for Mail Shield.Web ShieldWeb Shield activelyWeb Threat Shield - Magazinul web Chrome
The Internet has become the main instrument for communication and getting information all around the world. Still, there are a lot of threats for the user: viruses and other malicious software, as well as dangerous websites are all-present.AVG LinkScanner’s purpose is to allow safe browsing on the Internet. This software is a handy solution that enables you to search and surf the Web without worries. It protects you from ever-increasing online threats, by checking each web page in real time before it opens on your computer.First of all, AVG LinkScanner runs in the system tray, permanently keeping an eye on the websites you access. It protects your computer without any effort from your part, although you have the possibility to adjust its settings at any time.This protection module includes two components: Search-Shield and Surf-Shield. As the names suggest, these components, once activated, help you keep away from web-based attacks when searching or surfing the Internet.AVG LinkScanner offers easy access to settings, allowing you to optionally disable one or both of the protection methods, as well as the system tray notifications.You can integrate AVG LinkScanner with the compatible web browsers on your computer by installing an extension named AVG Safe Search. After enabling the addon, the program alerts you of any possible threat found on a website by displaying a rating and the risk category in your search engine. These are as follows: ‘Safe’, ‘Warning’ and 'Dangerous'. Still, you can access the website if you really want to.AVG LinkScanner includes on-demand scan feature, so you can easily scan a website address in order to detect threats on the page before you access it. The results are compatible with the ones other security products display. After viewing the scanning result, you can open the page directly from the main window of AVG LinkScanner.In order to be notified about any new threats that you may encounter online, you can perform an update of AVG LinkScanner at any time you want.Online threats are not all about viruses, as identity and personal information stealing have become a real issue. AVG LinkScanner is designed to preventWeb Threat Shield - Safe Web Browsing Chrome Extension
Secure your device with AI-powered protection Windows® Mac® AndroidTM iOS Chromebook AI-powered protection for all the ways you connect. Protect all your devicesProvide equal security to you PC, Mac, and mobile devices. Secure your transactionsBank online with Pay Guard to ensure the legitimacy of financial sites. Block web threatsDefend against ransomware and other online dangers. Shield your privacyBlock dangerous websites that can steal personal data. Safeguard your kidsAllow children to explore the web safely, with both time and content limits. Optimise performanceFix common problems and get everything running at top speed. Avoid fraud and scamsGuard against phishing emails. Compare products Stop ransomware and other threatsGet complete, multi-device protection against ransomware, viruses, dangerous websites, and identity thieves. An enhanced Folder Shield safeguards your valuable files and digital assets both locally and on cloud-synced folders like Dropbox®, Google Drive® and Microsoft® OneDrive®. Trend Micro stops more than 250 million threats daily i, so you can enjoy your digital life safely. Defend against the unknownOur cloud-based AI technology delivers highly effective and proactive protection against ever-evolving malware infections. You can depend on Trend Micro to defend against known and never-before-seen attacks, keeping you ahead of the rapidly changing threat landscape. Safeguard online paymentsEnhanced internet security protects you when shopping or banking online providing the ultimate security in connected world. Protect your whole mobile worldYour phone and tablet need protection too. Get advanced mobile security against viruses, spyware, thieves, and everything in-between with mobile security that delivers 100% malicious app detection.ii Want to know more? Compare Products System Requirements Compare products en_SG-SGD What you get Subscription term 1 year Secures PC, Mac, and mobile devices 1 device Antivirus, malware, ransomware & spyware protection yes Keeps children safe online yes NEW! Protects AI applications from tampering and abuse yes Secure VPN to protect your privacy Guard against identity theft with Dark Web monitoring 24x7 technical support Anti-track and Ad-blocker to stop third parties from collecting your data Filter out spam and scam text messages Warns you if a person in a video call is pretending to be someone else (Deepfakes) Cleans, optimises your PC or Mac Prices $49.00 Buy now What you get Subscription term 1 year Secures PC, Mac, and mobile devices Up to 4 devices Antivirus, malware, ransomware & spyware protection yes Keeps children safe online yes NEW! Protects AI applications from tampering and abuse yes Secure VPN to protect your privacy yes. Keeps you safe when browsing the web by identifying and blocking dangerous websites. Home/ Productivity/ Web Threat Shield. Web Threat Shield Web Threat Shield Keeps you safe when browsing the web by identifying and blocking dangerous websites. Home/ Productivity/ Web Threat Shield. Web Threat Shield Webroot Inc. Web Threat ShieldComments
Scans data that is transferred when you browse the internet to prevent malware from being downloaded and run on your PC. Avast Geek settings allow you to specify which action Web Shield performs when it detects a threat (virus, potentially unwanted program, potentially unwanted tool, or suspicious object). For each individual threat type, select an action from the drop-down menu:Abort connection (selected by default): Terminates your connection with the applicable website as soon as a potential threat is detected.Ask: Gives you the option to terminate the connection with the applicable website or remain connected when a potential threat is detected. Remaining connected may be risky. The following options allow you to further configure Web Shield behavior:Scan traffic from well-known browser processes only: With this option enabled, Web Shield only monitors HTTP traffic for the most common browsers.Show a notification window when an action is taken (enabled by default): You receive a notification from Avast each time Web Shield detects a threat. Script Shield protectionScript Shield prevents browsers and other applications from running potentially malicious scripts. This includes remote threats from the web and outside sources, local threats downloaded to your hard drive or in the browser cache, and scripts that come from encrypted connections.Tick or untick the relevant box to specify which browsers and applications are protected by Script Shield. Commonly used browsers, Adobe Acrobat Reader, and all other applications on your PC are protected by default.You can additionally configure report file settings individually for Web Shield.QuarantineQuarantine is an isolated space where you can safely store potentially dangerous files or send them to the Avast Threat Labs for analysis. Avast Geek settings allow you to specify the maximum size of files that Avast sends to Quarantine. The default value is 16384 KB.FirewallFirewall monitors all network traffic between your PC and the outside world to protect you from unauthorized communication and intrusions. You can configure the following aspects of Firewall behavior:Show notifications about newly created "block" rules (enabled by default): Sends an alert message each time a new rule related to prohibiting communication is created by the auto-decide feature.Internet Connection Sharing mode: Allows a trusted user to connect to the internet through your PC, or to troubleshoot problems with devices, such as a printer that is connected to the internet via your PC. Ticking this option opens certain ports which are usually closed, decreasing the level of security. Always untick this
2025-04-04Company Expands Ericom Global Cloud Platform Data Center Footprint to Support Growing Demand for Ericom’s Zero Trust Remote Browser Isolation SolutionNew York, NY (December 22, 2020) – Ericom Software, a leader in Zero Trust cloud cybersecurity solutions and a member of the Oracle Partner Network (OPN), announced today an expansion of its Ericom Global Cloud platform data center presence in the Middle East to support growing demand for Ericom Shield Remote Browser Isolation (RBI). These investments expand local access to Ericom’s globally distributed, multi-tenant cloud platform for businesses in the region, including existing Ericom customers supported by the company’s regional distribution and reseller partners. This announcement follows the company’s November press release noting it is experiencing record global demand for its Zero Trust security solutions as enterprises adopt Zero Trust and Secure Access Service Edge (SASE) security strategies.The rate of cyberattacks using malware designed to exploit web browser vulnerabilities has been dramatically accelerating. These types of attacks use zero-day malware embedded in the content of websites to deliver ransomware, exfiltrate data, disrupt operations, and more. The move to remote work, tied to COVID-19 office closures, unfortunately created additional vulnerabilities that make the risk of these attacks even greater. Ericom Shield RBI is uniquely capable of protecting endpoints and networks from just these sorts of attacks, preventing attacks targeting organizations via phishing emails, social media, and other stealthy vectors.Traditional web and email security approaches attempt to block threats by scanning traffic coming into networks, hoping to detect malware in order to protect devices. Ericom Shield RBI uses a fundamentally different approach that prevents 100% of web-based ransomware, zero-day threats, and phishing attacks from reaching endpoints. The solution executes web content in a remote, isolated cloud -based container, and only safe rendering information is sent to a device’s browser, providing a fully interactive, seamless user browsing experience. Whether users browse to a malicious site on their own or by clicking a URL embedded in a phishing email, they are completely safe since no web content is ever executed directly on their device.“Ransomware and other browser-based exploits delivered via the web and email are the key threat vectors that organizations need to secure,” said Ravi Pather, Ericom Vice President, Europe, and Middle East. “Ericom’s Zero Trust RBI solution integrates with solutions like secure web gateways and firewalls to ‘air gap’ endpoints from zero-day attacks being delivered by malicious websites that users visit while
2025-04-03Remove the file from your computer.Nothing: No action is taken during the scan; the threat is listed in your scan results and you can decide what to do later. The following options allow you to further configure File Shield behavior:You can additionally configure report file settings individually for File Shield.Mail ShieldMail Shield scans for threats in your incoming and outgoing email messages. Avast Geek settings allow you to specify which action Avast Antivirus performs when Mail Shield detects a threat (virus, potentially unwanted program, potentially unwanted tool, or suspicious object). For each threat type, select an action from the drop-down menu:Auto (selected by default): Run a sequence of actions (repair file; if not possible, then move to Quarantine; if not possible, then delete)Ask: Avast asks what you want to do with a detected threat before any action is taken.Nothing: No action is taken during the scan; the threat is listed in your scan results and you can decide what to do later.Move to Quarantine: Send the threat to Quarantine, where it cannot harm your system.Repair: Remove only malicious code attached to an otherwise safe file; this is not possible for files that are entirely malware.Delete: Permanently remove the file from your computer. The following options allow you to further configure Mail Shield behavior:Show a notification window when an action is taken (enabled by default): You receive a notification from Avast each time Mail Shield detects a threat.Scan archived messages when opening: Scans archived messages every time they are opened.Scan SSL connections (enabled by default): Enables scanning of emails sent or received using SSL/TLS encrypted connection. If disabled, only emails sent or received via unsecured connections are scanned. Export a Mail Shield certificateClick Perform to export a Mail Shield certificate from Avast Antivirus. This is useful for troubleshooting error messages about invalid server certificates from third party email clients, such as Mozilla Thunderbird.Port settingsIf Avast fails to intercept a malicious email or you notice that you are not receiving certain emails, you may need to correct the defined port numbers. Avast Geek allows you to edit the port numbers according to your email service provider or mail server configuration.If you do not know the port numbers that your mail service uses, contact your email provider or network administrator, or refer to the settings section of your email client.You can additionally configure report file settings individually for Mail Shield.Web ShieldWeb Shield actively
2025-04-22The Internet has become the main instrument for communication and getting information all around the world. Still, there are a lot of threats for the user: viruses and other malicious software, as well as dangerous websites are all-present.AVG LinkScanner’s purpose is to allow safe browsing on the Internet. This software is a handy solution that enables you to search and surf the Web without worries. It protects you from ever-increasing online threats, by checking each web page in real time before it opens on your computer.First of all, AVG LinkScanner runs in the system tray, permanently keeping an eye on the websites you access. It protects your computer without any effort from your part, although you have the possibility to adjust its settings at any time.This protection module includes two components: Search-Shield and Surf-Shield. As the names suggest, these components, once activated, help you keep away from web-based attacks when searching or surfing the Internet.AVG LinkScanner offers easy access to settings, allowing you to optionally disable one or both of the protection methods, as well as the system tray notifications.You can integrate AVG LinkScanner with the compatible web browsers on your computer by installing an extension named AVG Safe Search. After enabling the addon, the program alerts you of any possible threat found on a website by displaying a rating and the risk category in your search engine. These are as follows: ‘Safe’, ‘Warning’ and 'Dangerous'. Still, you can access the website if you really want to.AVG LinkScanner includes on-demand scan feature, so you can easily scan a website address in order to detect threats on the page before you access it. The results are compatible with the ones other security products display. After viewing the scanning result, you can open the page directly from the main window of AVG LinkScanner.In order to be notified about any new threats that you may encounter online, you can perform an update of AVG LinkScanner at any time you want.Online threats are not all about viruses, as identity and personal information stealing have become a real issue. AVG LinkScanner is designed to prevent
2025-03-27Is disabled by default to avoid false positive detections. Scan logsAvast scan logs contain details of events detected during a scan. By default, Avast creates scan logs each time you run a scan. Avast scan logs are stored in the following location:C:\ProgramData\AVAST Software\Avast\reportScan log settings apply to all scans in Avast Antivirus. The following options are available:Delete scan logs (enabled by default): Allows Avast to delete scan logs after a specified time period.Delete scan logs older than: Specify after how long Avast deletes scan logs.Delete temporary scan logs (enabled by default): Allows Avast to delete temporary scan logs after a specified time period.Delete temporary scan logs older than: Specify after how long Avast deletes temporary scan logs.Clear scan history: Click Perform to immediately delete all currently stored scan logs. Core ShieldsBehavior ShieldBehavior Shield monitors programs installed on your PC for suspicious behavior that may indicate the presence of malicious code. Configure how Behavior Shield deals with suspicious program behavior by selecting one of the following options from the drop-down menu:Always ask: Avast asks what you want to do with a detected threat before any action is taken.Automatically move detected threats to Quarantine: Threats that behave similarly to known threats listed on the Avast virus definitions database are moved to Quarantine, where they cannot harm your system.Automatically move known threats to Quarantine (enabled by default): Threats that are listed on the Avast virus definitions database are moved to Quarantine, where they cannot harm your system. File ShieldFile Shield actively scans all programs and files on your hard drive as they are opened, run, modified, and saved. Avast Geek settings allow you to specify which action File Shield performs when it detects a threat (virus, potentially unwanted program, potentially unwanted tool, or suspicious object). For each individual threat type, select an action from the drop-down menu:Fix automatically (selected by default): Run a sequence of actions (repair file; if not possible, then move to Quarantine; if not possible, then delete).Move to Quarantine: Send the threat to Quarantine, where it cannot harm your system.Repair: Remove only malicious code attached to an otherwise safe file — this is not possible for files that are entirely malware.Abort connection: If Avast detects that you are connected to a URL, game, or device that contains malware, the connection is stopped automatically.Ask: Avast asks what you want to do with a detected threat before any action is taken.Delete: Permanently
2025-03-27