Encryption decryption tool
Author: q | 2025-04-24
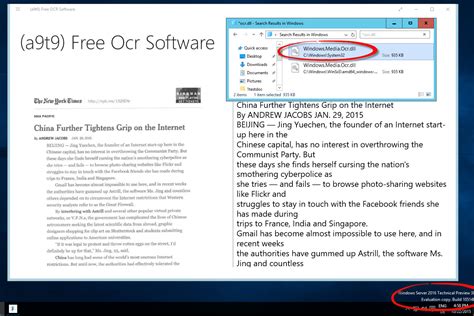
encryption-decryption-tool-gamma.vercel.app Topics windows encoding cryptography terminal encryption aes decoding password cmd aes-encryption encrypt decrypt decryption decrypter portable-executable encryption-tool encryption-decryption rust cryptography encryption decryption encryption-tool encryption-decryption decryption-tool encryption-decryption-tool. Updated ; Rust; sebastienrousseau / crypto-service. Sponsor Star 6. Code Issues Pull
PCK Encrypt Decrypt is an encryption and decryption tool.
While maintaining BitLocker encryption. After a BitLocker drive is decrypted, you can access, read, write, and manage files on the drive as usual. BitLocker decryption tools are commonly used in forensic investigations and data recovery scenarios.To decrypt a BitLocker-protected drive, you need to authenticate yourself with either the encryption password or recovery key. These credentials are essential for securely decrypting the drive. These keys are generated during the initial encryption setup and can be saved to a file, printed, or stored in a Microsoft account. If the recovery key or password is lost, decryption is typically not possible.If you are searching for a BitLocker decryption tool that can bypass the need for a password or recovery key, such a tool does not exist. The decryption of BitLocker-encrypted disks cannot be performed independently without the correct credentials.If you are using one of the following versions of Windows, you can use the built-in BitLocker decryption feature to decrypt your BitLocker disk and disable BitLocker encryption.Windows 11 Pro/Enterprise/EducationWindows 10 Pro/Enterprise/EducationWindows 8 Pro/EnterpriseWindows 7 Ultimate/EnterpriseWindows Server 2008 and later Standard/Enterprise/DatacenterBitLocker management interfaceWindows provides a built-in interface for managing BitLocker-encrypted drives. Users can decrypt a drive using the BitLocker management tool found in the Control Panel or the Settings app in Windows 10 and later versions.Step 1. Go to Control Panel or Settings and go to System and Security.Step 2. Click the BitLocker Drive Encryption to open it.Step 3. Select the encrypted drive you want to decrypt.Step 4. Click the Turn Off BitLocker and enter either the password or the recovery key when prompted.The decryption process may take some time depending on the size of the drive and the amount of data stored on it. Once decryption is complete, the drive will be converted back to its regular, unencrypted state. You can then access the data on the drive as usual.BitLocker decryption command line toolsWindows provides command-line tools such as manage-bde and PowerShell for handling BitLocker decryption and other related tasks. These tools require correctly inputting command lines to unlock a BitLocker-encrypted drive and disable encryption. They are particularly useful in scenarios where you cannot Be encrypted by ransomware that is not supported by ID Ransomware, you can always try searching the internet by using certain keywords (for example, a ransom message title, file extension, provided contact emails, crypto wallet addresses, etc.).Search for ransomware decryption tools:Encryption algorithms used by most ransomware-type infections are extremely sophisticated and, if the encryption is performed properly, only the developer is capable of restoring data. This is because decryption requires a specific key, which is generated during the encryption. Restoring data without the key is impossible. In most cases, cybercriminals store keys on a remote server, rather than using the infected machine as a host. Dharma (CrySis), Phobos, and other families of high-end ransomware infections are virtually flawless, and thus restoring data encrypted without the developers' involvement is simply impossible. Despite this, there are dozens of ransomware-type infections that are poorly developed and contain a number of flaws (for example, the use of identical encryption/decryption keys for each victim, keys stored locally, etc.). Therefore, always check for available decryption tools for any ransomware that infiltrates your computer.Finding the correct decryption tool on the internet can be very frustrating. For this reason, we recommend that you use the No More Ransom Project and this is where identifying the ransomware infection is useful. The No More Ransom Project website contains a "Decryption Tools" section with a search bar. Enter the name of the identified ransomware, and all available decryptors (if there are any) will be listed.Restore files with data recovery tools:Depending on the situation (quality of ransomware infection, type of encryption algorithm used, etc.), restoring data with certain third-party tools might be possible. Therefore, we advise you to use the Recuva tool developed by CCleaner. This tool supports over a thousand data types (graphics, video, audio, documents, etc.) and it is very intuitive (little knowledge is necessary to recover data). In addition, the recovery feature is completely free.Step 1: Perform a scan.Run the Recuva application and follow the wizard. You will be prompted with several windows allowing you to choose what file types to look for, which locations should be scanned, etc.AES encryption and decryption tools, AES encryption and decryption
The name of the malware family to which the infection belongs, whether it is decryptable, and so on.Example 1 (Qewe [Stop/Djvu] ransomware):Example 2 (.iso [Phobos] ransomware):If your data happens to be encrypted by ransomware that is not supported by ID Ransomware, you can always try searching the internet by using certain keywords (for example, a ransom message title, file extension, provided contact emails, crypto wallet addresses, etc.).Search for ransomware decryption tools:Encryption algorithms used by most ransomware-type infections are extremely sophisticated and, if the encryption is performed properly, only the developer is capable of restoring data. This is because decryption requires a specific key, which is generated during the encryption. Restoring data without the key is impossible. In most cases, cybercriminals store keys on a remote server, rather than using the infected machine as a host. Dharma (CrySis), Phobos, and other families of high-end ransomware infections are virtually flawless, and thus restoring data encrypted without the developers' involvement is simply impossible. Despite this, there are dozens of ransomware-type infections that are poorly developed and contain a number of flaws (for example, the use of identical encryption/decryption keys for each victim, keys stored locally, etc.). Therefore, always check for available decryption tools for any ransomware that infiltrates your computer.Finding the correct decryption tool on the internet can be very frustrating. For this reason, we recommend that you use the No More Ransom Project and this is where identifying the ransomware infection is useful. The No More Ransom Project website contains a "Decryption Tools" section with a search bar. Enter the name of the identified ransomware, and all available decryptors (if there are any) will be listed.Restore files with data recovery tools:Depending on the situation (quality of ransomware infection, type of encryption algorithm used, etc.), restoring data with certain third-party tools might be possible. Therefore, we advise you to use the Recuva tool developed by CCleaner. This tool supports over a thousand data types (graphics, video, audio, documents, etc.) and it is very intuitive (little knowledge is necessary to recover data). In addition, the recovery feature is completely free.Step 1: Perform a scan.Run. encryption-decryption-tool-gamma.vercel.app Topics windows encoding cryptography terminal encryption aes decoding password cmd aes-encryption encrypt decrypt decryption decrypter portable-executable encryption-tool encryption-decryption rust cryptography encryption decryption encryption-tool encryption-decryption decryption-tool encryption-decryption-tool. Updated ; Rust; sebastienrousseau / crypto-service. Sponsor Star 6. Code Issues PullDCrypt: Encryption and decryption tool that
XP 1.7.394 Date Released: Dec 13, 2021 Status: Major Update Release Notes: Improved support for Windows 10. updated: Use themes for Explorer shell menu items on Windows Vista and later. fixed: Removed incorrectly created registry keys. Software: File Encryption XP 1.7.393 Date Released: Nov 16, 2021 Status: Major Update Release Notes: Improved support for Windows 10. updated: Use themes for Explorer shell menu items on Windows Vista and later. fixed: Removed incorrectly created registry keys. Most popular windows encryption software in Encryption Tools downloads for Vista BestCrypt 9.09.3 download by Jetico, Inc. ... by Jetico, Inc., is a robust and user-friendly encryption software designed to secure sensitive data through the creation ... users. BCArchive supports a wide range of encryption algorithms, including AES (Advanced Encryption Standard), Blowfish, and ... View Details Download Folder Encryption Fairy 4.6 download by Soarersoft Software Studio [Folder Encryption Fairy] is an simple-to-use and reliable encryption utility to password protect folders or encrypt files ... combinational encrypt(decrypt). The main functional moduels include: fast encryption/decryption,high density encryption/decryption,portable encryption/decryption,mask folder,hide folder,and wipe out folder. ... View Details Download The Enigma Protector 7.80 download by The Enigma Protector Developers Team ... system for licensing and protecting executable files for Windows. The Enigma Protector is an essential tool for every developer of commercial software and shareware for Windows. The Enigma Protector includes a wide range of ... type: Demo ($249.00) categories: protector, packer, software, shareware, license, registration, protect, packing, protection, encryption, enigma View Details Download The Enigma Protector x64 7.80 download by The Enigma Protector Developers Team ... system for licensing and protecting executable files for Windows. The Enigma Protector is an essential tool for every developer of commercial software and shareware for Windows. The Enigma Protector includes a wide range of ... type: Demo ($249.00) categories: protector, packer, software, Crypt-ItA simple AES-CBC encryption tool for documentsTable of ContentsInstallationUsageEncryptionDecryptionRequirementsInstallationTo install Crypt-It, run the following command in your terminal:pip install -r requirements.txtThis will install all necessary dependencies for running the program.UsageEncryptionTo encrypt a file using Crypt-It, simply run the following command:python crypt-it.py -e [input_file]Replace [input_file] with the path to the file you want to encrypt. You will be prompted to enter an encryption password and confirm it.Example:Enter encryption password: [yourpassword]Confirm encryption password: [yourpassword]File encrypted and saved to example.doc.encThe original file [example.doc] will be replaced with the encrypted version (example.doc.enc).DecryptionTo decrypt a file, run the following command:python crypt-it.py -d [input_file]Replace [input_file] with the path to the .enc file you want to decrypt. You will be prompted to enter the decryption password.Example:Enter decryption password:[yourpassword]File decrypted and saved to example.docThe original encrypted file (example.doc.enc) will be replaced with the decrypted version (example.doc).RequirementsPython 3.6+and cryptography libraries included in requirements.txtNote: Make sure to store your encryption/decryption passwords securely, as they cannot be recovered if lost.Free encryption-decryption tool with
Data using a tool developed by cyber security researcher, Michael Gillespie, however, since the encryption mechanism has been slightly changed (hence the new version, released in August, 2019), the decrypter no longer works and it is not supported anymore.If your data has been encrypted by an older version, you might be able to restore it with the another tool developed by Emsisoft and Michael Gillespie. It supports a total of 148 Djvu's variants and you can find more information, as well as download link and decryption instructions in Emsisoft's official page.Screenshot of Djvu decryption tool by Emsisoft and Michael Gillespie:Additionally, Emsisoft is now providing a service that allows to decrypt data (again, only if it was encrypted by Djvu variants released before August, 2019) for those victims who have a pair of the same file before and after the encryption. All victims have to do is upload a pair of original and encrypted file to Emsisoft's Djvu decryption page and download the aforementioned decryption tool (the download link will be provided after uploading files).Note that the file processing may take some time so be patient. It is also worth mentioning that the system must have an Internet connection during the entire decryption process, otherwise it will fail.Screenshot of Emsisoft's Djvu decryption service page:Some victims state that they've successfully restored a part of encrypted data using PhotoRec tool developed by CGSecurity (Christophe Grenier). You can download this tool from CGSecurity's official website.Screenshot of PhotoRec application:Now it is worth noting that Djvu ransomware does not encrypt the entire file. Instead, it encrypts only a portion (start) of the file, thereby making it unusable. Luckily, in some cases it is possible to restore other part of the file, which is not encrypted. This is useful when it comes to audio/video files, because even though the start won't be restored, you'll still be able to use most of it.To restore audio/video data we advise you to use Media_Repair tool developed by DiskTuna. This tool is extremely simple and completely free. You can find the user manual as well as download the tool directly from DiskTuna's website.Screenshot of Media_Repair application developed by DiskTuna:G DATA company has also released a "vaccine" capable of preventing Djvu ransomware from encrypting data. This does not mean that the malware won't be able to enter the system or to perform other actions (e.g., change system settings). However, the encryption will be prevented nevertheless. You can download the vaccination tool from this GitHub page.Screenshot of G DATA's Djvu ransomware vaccination tool:Video showing how to remove Nbwr ransomware using Combo Cleaner:Nbwr ransomware removal:Instant automatic malware removal:Manual threat removal might be a lengthy and complicated process that requires advanced IT skills. Combo CleanerEncryption and Decryption Tool - GitHub
And you will be provided with various details, such as the name of the malware family to which the infection belongs, whether it is decryptable, and so on.Example 1 (Qewe [Stop/Djvu] ransomware):Example 2 (.iso [Phobos] ransomware):If your data happens to be encrypted by ransomware that is not supported by ID Ransomware, you can always try searching the internet by using certain keywords (for example, a ransom message title, file extension, provided contact emails, crypto wallet addresses, etc.).Search for ransomware decryption tools:Encryption algorithms used by most ransomware-type infections are extremely sophisticated and, if the encryption is performed properly, only the developer is capable of restoring data. This is because decryption requires a specific key, which is generated during the encryption. Restoring data without the key is impossible. In most cases, cybercriminals store keys on a remote server, rather than using the infected machine as a host. Dharma (CrySis), Phobos, and other families of high-end ransomware infections are virtually flawless, and thus restoring data encrypted without the developers' involvement is simply impossible. Despite this, there are dozens of ransomware-type infections that are poorly developed and contain a number of flaws (for example, the use of identical encryption/decryption keys for each victim, keys stored locally, etc.). Therefore, always check for available decryption tools for any ransomware that infiltrates your computer.Finding the correct decryption tool on the internet can be very frustrating. For this reason, we recommend that you use the No More Ransom Project and this is where identifying the ransomware infection is useful. The No More Ransom Project website contains a "Decryption Tools" section with a search bar. Enter the name of the identified ransomware, and all available decryptors (if there are any) will be listed.Restore files with data recovery tools:Depending on the situation (quality of ransomware infection, type of encryption algorithm. encryption-decryption-tool-gamma.vercel.app Topics windows encoding cryptography terminal encryption aes decoding password cmd aes-encryption encrypt decrypt decryption decrypter portable-executable encryption-tool encryption-decryptionAES Encryption and Decryption Tool
Home Security AutoKrypt Review Technical Buy Edit AutoKrypt: Seamless File Encryption Automation AutoKrypt provides a powerful yet easy-to-use solution for automating file encryption and decryption processes, making it ideal for businesses and individuals looking to secure sensitive information. image/svg+xml 2025 Editor's Rating AutoKrypt by Hitek SoftwareAutoKrypt by Hitek Software is a comprehensive encryption and decryption tool designed to provide users with a secure way to protect their sensitive data. Whether you need to encrypt files for safe storage or securely share them with others, AutoKrypt offers a wide range of features to meet your needs.Key Features: Automated Encryption and Decryption: AutoKrypt allows users to set up automated tasks for encrypting and decrypting files, saving time and ensuring that sensitive data remains secure. Multiple Encryption Algorithms: The software supports a variety of encryption algorithms, including AES, Blowfish, and DES, giving users flexibility in choosing the level of security they need for their data. Batch Processing: Users can encrypt or decrypt multiple files at once, making it easy to protect large amounts of data quickly and efficiently. File Synchronization: AutoKrypt includes file synchronization capabilities, allowing users to keep their encrypted files up to date across multiple devices. Integration with Windows Explorer: The software integrates seamlessly with Windows Explorer, making it easy to encrypt and decrypt files directly from the file manager.Benefits: Enhanced Security: With strong encryption algorithms and automated tasks, AutoKrypt helps users keep their data secure from unauthorized access. Time Savings: The software's batch processing and automation features save users time by streamlining the encryption and decryption process. User-Friendly Interface: AutoKrypt's intuitive interface makes it easy for users of all levels of technical expertise to protect their data effectively. Flexible Encryption Options: Users can choose from a range of encryption algorithms to find the level of security that best suits their needs.Final Verdict:AutoKrypt by Hitek Software is a powerful encryption tool that offers a wide range of features to help users protect their sensitive data. With automated tasks, multiple encryption algorithms, and batch processing capabilities, this software provides both security and convenience for individuals and businesses looking to keep their information safe. Overview AutoKrypt is a Shareware software in the category Security developed by Hitek Software.The latest version of AutoKrypt is 11.1, released on 04/30/2015. It was initially added to our database on 02/22/2008.AutoKrypt runs on the following operating systems: Windows. The download file has a size of 42MB.AutoKrypt has notComments
While maintaining BitLocker encryption. After a BitLocker drive is decrypted, you can access, read, write, and manage files on the drive as usual. BitLocker decryption tools are commonly used in forensic investigations and data recovery scenarios.To decrypt a BitLocker-protected drive, you need to authenticate yourself with either the encryption password or recovery key. These credentials are essential for securely decrypting the drive. These keys are generated during the initial encryption setup and can be saved to a file, printed, or stored in a Microsoft account. If the recovery key or password is lost, decryption is typically not possible.If you are searching for a BitLocker decryption tool that can bypass the need for a password or recovery key, such a tool does not exist. The decryption of BitLocker-encrypted disks cannot be performed independently without the correct credentials.If you are using one of the following versions of Windows, you can use the built-in BitLocker decryption feature to decrypt your BitLocker disk and disable BitLocker encryption.Windows 11 Pro/Enterprise/EducationWindows 10 Pro/Enterprise/EducationWindows 8 Pro/EnterpriseWindows 7 Ultimate/EnterpriseWindows Server 2008 and later Standard/Enterprise/DatacenterBitLocker management interfaceWindows provides a built-in interface for managing BitLocker-encrypted drives. Users can decrypt a drive using the BitLocker management tool found in the Control Panel or the Settings app in Windows 10 and later versions.Step 1. Go to Control Panel or Settings and go to System and Security.Step 2. Click the BitLocker Drive Encryption to open it.Step 3. Select the encrypted drive you want to decrypt.Step 4. Click the Turn Off BitLocker and enter either the password or the recovery key when prompted.The decryption process may take some time depending on the size of the drive and the amount of data stored on it. Once decryption is complete, the drive will be converted back to its regular, unencrypted state. You can then access the data on the drive as usual.BitLocker decryption command line toolsWindows provides command-line tools such as manage-bde and PowerShell for handling BitLocker decryption and other related tasks. These tools require correctly inputting command lines to unlock a BitLocker-encrypted drive and disable encryption. They are particularly useful in scenarios where you cannot
2025-03-25Be encrypted by ransomware that is not supported by ID Ransomware, you can always try searching the internet by using certain keywords (for example, a ransom message title, file extension, provided contact emails, crypto wallet addresses, etc.).Search for ransomware decryption tools:Encryption algorithms used by most ransomware-type infections are extremely sophisticated and, if the encryption is performed properly, only the developer is capable of restoring data. This is because decryption requires a specific key, which is generated during the encryption. Restoring data without the key is impossible. In most cases, cybercriminals store keys on a remote server, rather than using the infected machine as a host. Dharma (CrySis), Phobos, and other families of high-end ransomware infections are virtually flawless, and thus restoring data encrypted without the developers' involvement is simply impossible. Despite this, there are dozens of ransomware-type infections that are poorly developed and contain a number of flaws (for example, the use of identical encryption/decryption keys for each victim, keys stored locally, etc.). Therefore, always check for available decryption tools for any ransomware that infiltrates your computer.Finding the correct decryption tool on the internet can be very frustrating. For this reason, we recommend that you use the No More Ransom Project and this is where identifying the ransomware infection is useful. The No More Ransom Project website contains a "Decryption Tools" section with a search bar. Enter the name of the identified ransomware, and all available decryptors (if there are any) will be listed.Restore files with data recovery tools:Depending on the situation (quality of ransomware infection, type of encryption algorithm used, etc.), restoring data with certain third-party tools might be possible. Therefore, we advise you to use the Recuva tool developed by CCleaner. This tool supports over a thousand data types (graphics, video, audio, documents, etc.) and it is very intuitive (little knowledge is necessary to recover data). In addition, the recovery feature is completely free.Step 1: Perform a scan.Run the Recuva application and follow the wizard. You will be prompted with several windows allowing you to choose what file types to look for, which locations should be scanned, etc.
2025-04-05The name of the malware family to which the infection belongs, whether it is decryptable, and so on.Example 1 (Qewe [Stop/Djvu] ransomware):Example 2 (.iso [Phobos] ransomware):If your data happens to be encrypted by ransomware that is not supported by ID Ransomware, you can always try searching the internet by using certain keywords (for example, a ransom message title, file extension, provided contact emails, crypto wallet addresses, etc.).Search for ransomware decryption tools:Encryption algorithms used by most ransomware-type infections are extremely sophisticated and, if the encryption is performed properly, only the developer is capable of restoring data. This is because decryption requires a specific key, which is generated during the encryption. Restoring data without the key is impossible. In most cases, cybercriminals store keys on a remote server, rather than using the infected machine as a host. Dharma (CrySis), Phobos, and other families of high-end ransomware infections are virtually flawless, and thus restoring data encrypted without the developers' involvement is simply impossible. Despite this, there are dozens of ransomware-type infections that are poorly developed and contain a number of flaws (for example, the use of identical encryption/decryption keys for each victim, keys stored locally, etc.). Therefore, always check for available decryption tools for any ransomware that infiltrates your computer.Finding the correct decryption tool on the internet can be very frustrating. For this reason, we recommend that you use the No More Ransom Project and this is where identifying the ransomware infection is useful. The No More Ransom Project website contains a "Decryption Tools" section with a search bar. Enter the name of the identified ransomware, and all available decryptors (if there are any) will be listed.Restore files with data recovery tools:Depending on the situation (quality of ransomware infection, type of encryption algorithm used, etc.), restoring data with certain third-party tools might be possible. Therefore, we advise you to use the Recuva tool developed by CCleaner. This tool supports over a thousand data types (graphics, video, audio, documents, etc.) and it is very intuitive (little knowledge is necessary to recover data). In addition, the recovery feature is completely free.Step 1: Perform a scan.Run
2025-04-23